Desktop Phishing-Silent Phishing Technique without fear of getting blocked by free hosting and link distribution panic
 You may already be familiar with the phishing technique as I have posted some articles over it, However still you don’t understood it then I should tell you here again that phishing is such an act where hacker makes a duplicate page I must say login page of any website and in the login fields he makes some changings like he embeds a logger script in those login forum fields, thus as a result what you type in those fields is logged and are pasted in a text file on that server where that phishing i-e duplicate page is hosted to fool you. Thus you email and password are sent to hacker as those login fields are for “email address” and “password” ultimately in the end you are redirected to original login page. You should read following posts to understand this in detail:-
You may already be familiar with the phishing technique as I have posted some articles over it, However still you don’t understood it then I should tell you here again that phishing is such an act where hacker makes a duplicate page I must say login page of any website and in the login fields he makes some changings like he embeds a logger script in those login forum fields, thus as a result what you type in those fields is logged and are pasted in a text file on that server where that phishing i-e duplicate page is hosted to fool you. Thus you email and password are sent to hacker as those login fields are for “email address” and “password” ultimately in the end you are redirected to original login page. You should read following posts to understand this in detail:-Explaining phishing to new-bies ( Demonstrating by Facebook phishing hack)
Gmail Hacking By Phishing Page
Tab Napping ( A new phishing technique )
Drawback of such phishing techniques:-
Such techniques need such a hosting whose TOS can’t be broken when we upload such pages.This needs a link to be spread which takes victim to the phisher page.
This are also now recognized more easily as the URL of the browser is not trustable since now many people are aware of such attacks and modern browsers can understand phishing well now.
You must be an expert to implement such attacks successfully if you are a newbie you can’t fool victim by just following simple guides provided at various sites. So, this old phishing technique is also useful we can’t deny its use but it gets bit tricky to implement it.
What is Desktop Phishing?
Well, it is a kind of phishing where you have to just replace some text in the hosts file located in Windows directory in the victim machine and whenever he goes to the real website like yahoo.com then real website won’t open instead of it the phishing page will open which will be hosted in your computer (Or any other hosting purchased one as you prefer as rest steps are same as in common phishing).A diagram to differentiate between Desktop phishing and Common Phishing:-

I created this simple diagram to differentiate between common phishing and desktop one, Hope you may get it now clearly.
Steps to Perform Desktop Phishing:-
Following are the steps to perform desktop phishing which are explained in quite good manner.1. Make your computer a server to host files or say phishing page:-
I have already covered this section in one of my last posts, if you haven’t read that on how to convert your computer into server to host your own webpages then you must read:-How to: Convert Computer in WebServer - Host Webpages For Free
This is quite good step as in this case you won’t break TOS
2. What is hosts file and how to exploit them for desktop phishing-Basic Scheme:-
A hosts file is a file which contains domain names and IP addresses associated with them.Like when we visit a website like www.website.com then a query is sent to the DNS (Domain Name Server) in order to look for the IP address which may be associated with that domain to take you to the desired website. But before this query the local computer is checked for the IP address associated with that domain, and the file which is checked for this purpose it the hosts file located here:- C:\Windows\System32\drivers\etc\Now lets make an entry in hosts file, you can use simple notepad to edit it, well I am using notepad++ for this purpose. I have opened hosts file by right clicking it and then opening it my notepad++ and after that I have added the IP address and the URL along which I want to associate that IP address. I think you have understood that what we are going to do. See sample below, when victim will open www.hackersthirst.com he will be taken to the IP address(111.111.111.50) in Hosts file as below:-
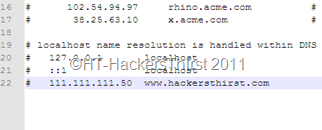
3. Creating an SFX archive to replace real hosts file with our own created in victim computer:-
Now, you have converted your computer in a webserver to host files and thus you have a public IP address of your server using which you can associate any domain name with your public id, yes we are going to exploit hosts file. Now, what we shall do is this, that we shall copy our hosts file and will modify it ass below by assigning our IP address where required phishing page is uploaded lets say its yahoo phisher:-
So, your modified hosts file is created now, lets plan out a way to replace victim’s hosts file with it, there are many ways, but I shall tell you one here of creating a solid archive by WinRAR you can download it here.
After installing WinRAR right click on the modified hosts file and then “Add to archive” after this tick create “SFX archive” like I did:-





After this create the archive and send it to the victim and as a result his hosts file will be replaces you can bind this file to any other exe or picture just read this post:-
Hide archives and RAT’s by using Binders
Whenever he will open the website in his computer i-e yahoo.com your own phishing page will come in front of him which will be hosted in your own computer. So, he will be hacked without any notice.
What you got from this post? or Countermeasures to remain safe from such attacks:-
So, now you know this type of attacks also exists to never blindly trust any exe file or any picture always explore the files given by any stranger if you see that the icon is of a .jpg file and extension is .exe then it surely means that the file is binded. So, I must say that best security is always from you hackers just make use of our own foolishness.Subscribe to us to get all such latest updates, similarly as I told you in one of the previous posts, I,ll tell you some ways using which the hacker can send you such files and your computer can be monitored, I must say some social engineering tricks, so stay in touch, and read this also:-
Social Engineering-How its done and How to remain safe..!
Comments
joomla seo
fnsupg 909132 [url=http://www.oakleyssunglassessoutlet.com/]sunglass oakley[/url] 714157 [url=http://www.cheapsoakleysunglassess.com/]oakley sunglass outlet[/url]
jecbee 526497 [url=http://www.oakleyssunglassessoutlet.com/]cheap oakley sunglass[/url] 573106 [url=http://www.cheapsoakleysunglassess.com/]oakley sunglass bag[/url]
kfbntk 065787 [url=http://www.oakleyssunglassessoutlet.com/]oakley sunglass strap[/url] 212879 [url=http://www.cheapsoakleysunglassess.com/]oakley sunglass[/url]
htxxug 852236 [url=http://www.oakleyssunglassessoutlet.com/]cheap oakley sunglass[/url] 148595 [url=http://www.cheapsoakleysunglassess.com/]sunglass oakley[/url]
qlvdna 462283 [url=http://www.oakleyssunglassessoutlet.com/]oakley sunglass sale[/url] 957281 [url=http://www.cheapsoakleysunglassess.com/]oakley sunglass[/url]
xriqwz 962036 [url=http://www.oakleyssunglassessoutlet.com/]oakley sunglass outlet[/url] 291611 [url=http://www.cheapsoakleysunglassess.com/]oakley sunglass bag[/url]
ygrrtj 494211 [url=http://www.oakleyssunglassessoutlet.com/]oakley sunglass stores[/url] 622797 [url=http://www.cheapsoakleysunglassess.com/]oakley sunglass[/url]